Introduction
In today's digital landscape, security is paramount. Cyber threats are continuously evolving, making it essential for software developers to prioritize security from the inception of a project through its entire lifecycle. The Open Web Application Security Project (OWASP) provides invaluable resources to help developers address and fix security issues correctly. This blog will delve into how to effectively utilize OWASP guidelines and tools to enhance software security.
Understanding OWASP
OWASP is a non-profit foundation focused on improving software security. It offers a wide array of free resources, including:
- OWASP Top Ten: A list of the ten most critical web application security risks.
- OWASP Application Security Verification Standard (ASVS): A framework for testing the security of applications.
- OWASP Software Assurance Maturity Model (SAMM): A guide to building security into software development processes.
- OWASP Dependency-Check: A tool for identifying project dependencies and checking if they contain known vulnerabilities.
Identifying Security Issues
The first step in fixing security issues is to identify them accurately. OWASP provides several tools and guidelines for this purpose:
- Static Application Security Testing (SAST): These tools analyze source code for security vulnerabilities. OWASP recommends tools like OWASP Code Pulse and OWASP Orizon.
- Dynamic Application Security Testing (DAST): These tools test running applications to find vulnerabilities. OWASP Zed Attack Proxy (ZAP) is a popular choice.
- Software Composition Analysis (SCA): Tools like OWASP Dependency-Check help in identifying vulnerabilities in third-party libraries and frameworks.
Prioritizing Security Fixes
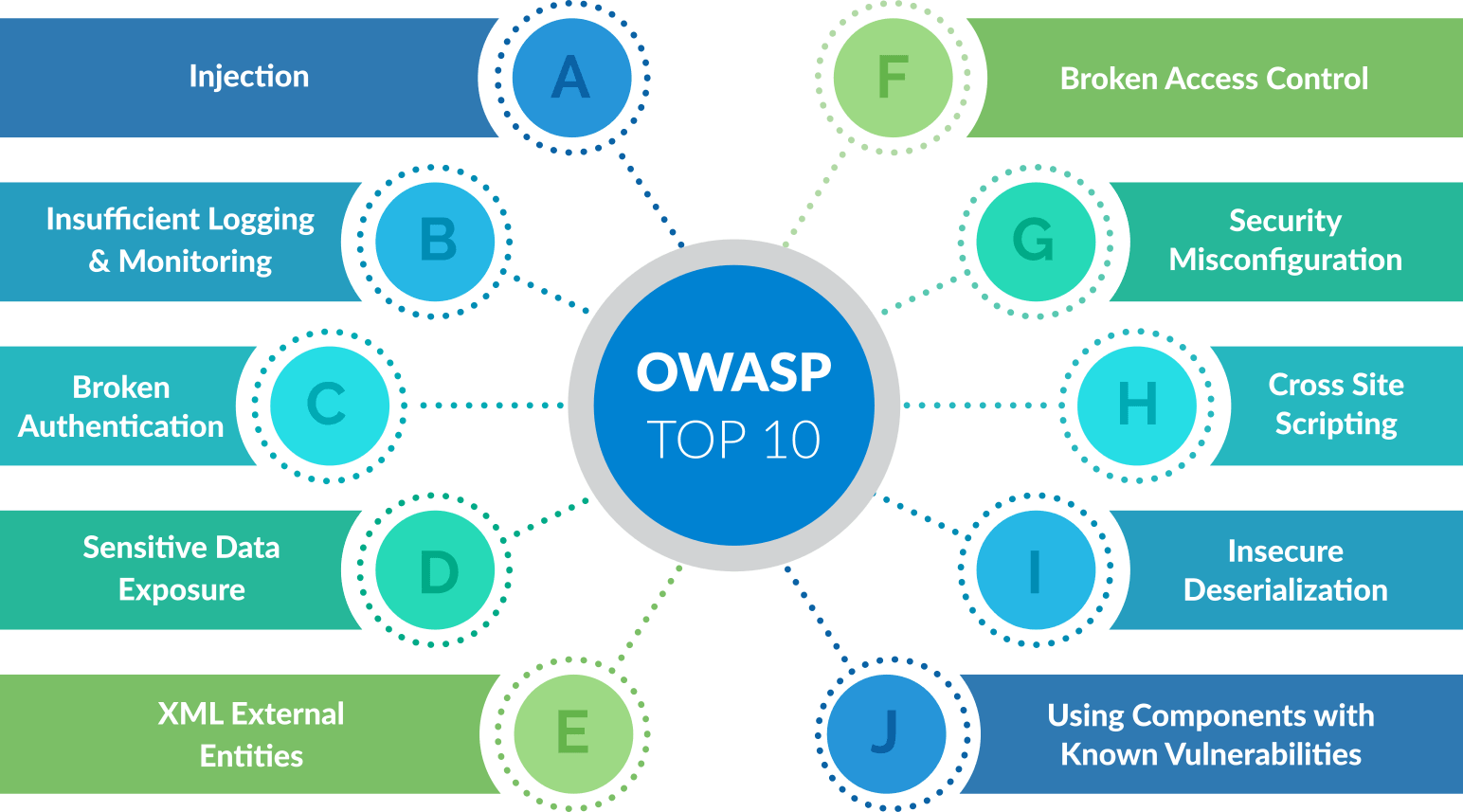
Not all security issues have the same impact. Prioritizing them is crucial to allocate resources effectively. The OWASP Top Ten is an excellent starting point for understanding the most critical risks. Here's a brief overview:
- Injection: Including SQL, NoSQL, OS, and LDAP injection flaws.
- Broken Authentication: Issues that compromise password, session tokens, or keys.
- Sensitive Data Exposure: Insecure storage and transmission of sensitive data.
- XML External Entities (XXE): Flaws in processing XML data.
- Broken Access Control: Failures to enforce proper restrictions on authenticated users.
- Security Misconfiguration: Incorrect configuration of security controls.
- Cross-Site Scripting (XSS): Injection of malicious scripts into web pages.
- Insecure Deserialization: Flaws that allow remote code execution.
- Using Components with Known Vulnerabilities: Reliance on libraries with known security flaws.
- Insufficient Logging & Monitoring: Lack of adequate logging and alerting mechanisms.
Fixing Security Issues Correctly
1. Injection Attacks
- Sanitize Inputs: Ensure all inputs are validated and sanitized.
- Parameterized Queries: Use prepared statements and parameterized queries.
- ORMs: Use Object-Relational Mappers (ORMs) that automatically handle input sanitization.
2. Broken Authentication
- Strong Password Policies: Enforce strong password creation and storage policies.
- Multi-Factor Authentication: Implement MFA wherever possible.
- Session Management: Use secure tokens and properly handle session lifetimes.
3. Sensitive Data Exposure
- Encryption: Encrypt data at rest and in transit using strong cryptographic standards.
- Secure APIs: Use HTTPS and secure API endpoints.
4. XML External Entities (XXE)
- Disable External Entities: Configure XML parsers to disable external entity processing.
- Use JSON: Prefer JSON over XML for data interchange.
5. Broken Access Control
- Least Privilege: Implement the principle of least privilege.
- Role-Based Access Control: Use RBAC to manage user permissions.
6. Security Misconfiguration
- Default Configurations: Change default credentials and configurations.
- Automated Scanning: Regularly use automated tools to scan for misconfigurations.
7. Cross-Site Scripting (XSS)
- Output Encoding: Encode data before rendering it on the client side.
- Content Security Policy (CSP): Implement CSP to prevent script execution.
8. Insecure Deserialization
- Avoid Deserialization: Where possible, avoid deserialization of untrusted data.
- Integrity Checks: Implement checks to ensure data integrity.
9. Using Components with Known Vulnerabilities
- Regular Updates: Keep libraries and components up to date.
- Vulnerability Scanners: Use tools like OWASP Dependency-Check to identify vulnerabilities.
10. Insufficient Logging & Monitoring
- Comprehensive Logging: Log all critical actions and security-relevant events.
- Alerting Systems: Implement real-time alerting and monitoring systems.
Conclusion
Addressing and fixing security issues correctly is an ongoing process that requires diligence and adherence to best practices. By leveraging OWASP's comprehensive resources, developers can significantly enhance the security posture of their applications. Prioritizing security, staying informed about the latest threats, and continuously updating and testing applications are key to safeguarding against cyber threats.
Integrating OWASP guidelines and tools into your development workflow not only helps in fixing current security issues but also in building a robust foundation for secure software development.